A research team recently discovered that the ‘autofill’ feature in Android-based apps accidentally leaked login details to some apps that host the webpage. The paper ‘AutoSpill: Credential Leakage from Mobile Password Managers’ won the best paper award at the ACM Conference on Data and Application Security and Privacy (Codaspy) 2023.
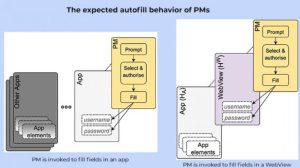
According to a statement from the International Institute of Information Technology, Hyderabad, every time an app loads a login page in WebView, and an autofill request is generated, the password manager (PM) and operating systems get disoriented about the target page for filling in the login details. Basically, the app loading the WebView could obtain access to people’s sensitive information.
Prof Ankit Gangwal, lead author, explained that ‘if one tries to log into a music app on a mobile device, and uses the option of “login via Google or Facebook”, the music app will open Google or Facebook login page inside itself (i.e., within the music app) via WebView. When the PM is invoked to autofill the credentials, ideally it should autofill only into the Google or Facebook page that has been loaded. But we found that the autofill operation could accidentally expose the credentials to the base app, which in this case is your music app.’
The professor emphasized that ‘even without phishing, any malicious app that asks you to login via another site, like Google or Facebook, can automatically get access to sensitive information.’
‘We brought this to the notice of Google as well as the password managers, who then acknowledged the security breach,’ Prof Gangwal said. He added that it is a challenge that needs a close-knit cooperation between the password managers and operating systems.
The researchers are currently analyzing the possibility of a reverse AutoSpill attack. This is a scenario where one can obtain sensitive credentials from the hosting app to the hosted webpage.
By Marvellous Iwendi.
From Deccan Chronicle